ALL IN ONE
All-IN-ONE is THE IT Security Solution from PT SYDECO it is based on the principles
of ZERO-TRUST and is designed to prevent cyber-attacks such as Ransomware or data breaches, in the
event of an attack, allowing computer networks to continue to function by preventing viruses or
worms have any effect and prevent lateral contamination in the tissue.
All-IN-ONE IT Security Solution from PT Sydeco focuses on protecting the
resources (all data and computing services) of an establishment or enterprise, such as assets, data,
services, workflows, networks. Sydeco's ALL-IN-ONE IT Security Solution protects all enterprise
assets (devices, applications, virtual and cloud components) and subjects (end users, applications
and other non-human entities requesting information from resources).
All-IN-ONE Cybersecurity Solution from PT Sydeco secures all
communications, all data transfers regardless of where the network is located. All-IN-ONE IT
Security Solution from PT Sydeco is fully auditable, so that the state of assets as well as the
integrity and security posture of all owned and related assets can be observed.
PT Sydeco's ALL-IN-ONE IT Security Solution, thanks to its Micro Segmentation Architecture
to reduce the attack surface, limits attack impact and prevents lateral contamination within the
enterprise.
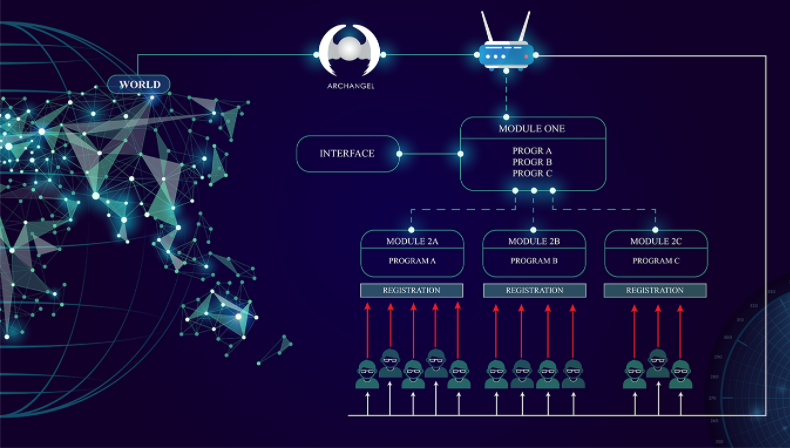
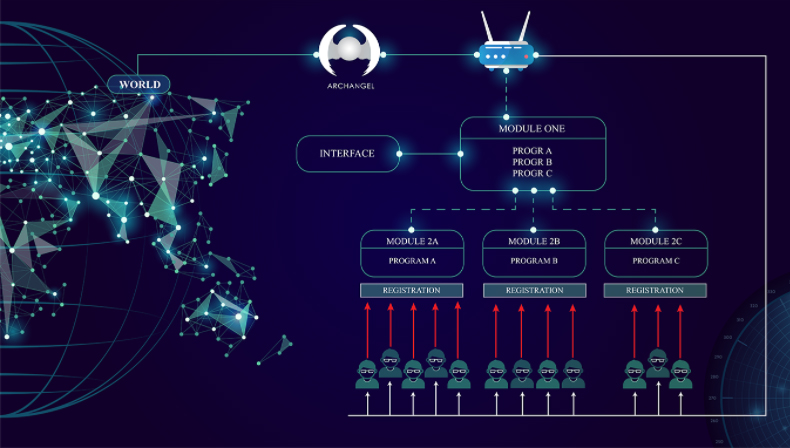
Figure 1: ALL-IN-ONE (Archangel, SP-One & SST) protect Programs and Data
A. Network Security
The company's computer network, in any enterprise or establishment is protected by
ARCHANGEL©, an advanced firewall created by PT SYDECO which is one of the
components of the All-IN-ONE IT Security Solution.
ARCHANGEL© protects servers, computers and other connected objects from
cyber-attacks originating from the outside world and prevents the spread of lateral virus
contamination within the company.
Servers, computers that are on the company's internal network and which are connected to
ARCHANGEL© itself are protected by SP-One©.
SP-One©, which is another component of the ALL-IN-ONE IT Security Solution, is a
program and system that creates an airtight, secure shelter around source code or programs used in
office, administration, or university computer networks. Cloud and in SaaS.
SP-One© protects servers, programs or Source Code against any cyber-attacks from the outside world
and against those coming from within private computer network.
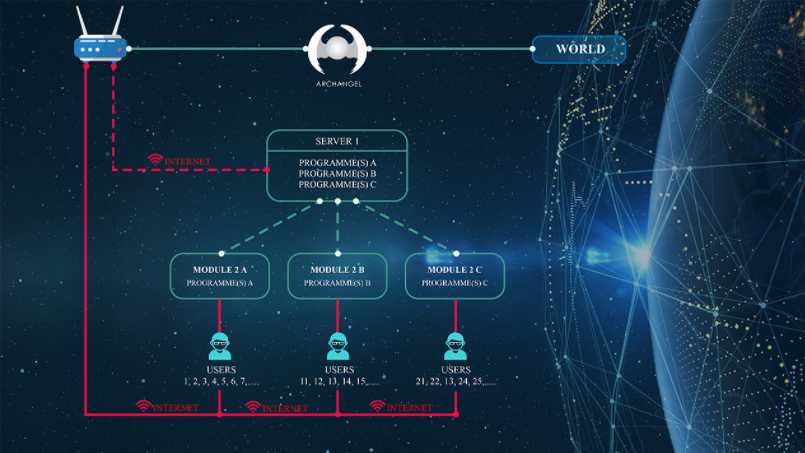
Figure 2: ALL-IN-ONE (Archangel, SP-One & SST) protect Servers
Enterprise computer network security is enhanced by the ALL-IN-ONE Micro Segmentation
Architecture. Thanks to the Micro Segmentation Architecture, users can only access the
servers they need to work on and after being registered as authorized users.

Figure 3: Zero Trust & Micro Segmentation protect programs against lateral
contamination
It follows that if a user accidentally or intentionally contaminates his computer, the virus or worm
he has downloaded can only try to attack the server he is connected to. And this server is protected
by SP-One, so not only the user will not be able to infect the server connected to it but also no
other server in the network.
B. Mobile Data Security
All data moving within the internal network or outside, in the outside world, is protected by SST©,
Secure System of Transmission, which is another creation of PT SYDECO, and delivered inside the VPN.
SST© protects data by encrypting it without using a key, without any third party intervention, using
artificial intelligence to do so.
SST© also protects all passwords used in the All-IN-ONE IT Security System.
VPN are created by ARCHANGEL and encrypted by SST©.
This is E2E protection and only the receiver can read the data. The data will disappear if someone
tries to intercept it.
C. Security On data at rest
Backup Data is protected by SP-One and by Logic Micro Segmentation Architecture used by ALL-IN-ONE
systems. Finally all data even when at rest, is encrypted by SST©.
D. Security Of The Industrial Control Systems (ICS) Endpoints'
ALL-IN-ONE protects ICS endpoints from SCADA (Monitoring Control And Data
Acquisition) or DCS (Distributed Control System) against worms such as StuxNet, or viruses such as
ShaMoon or Trojan Horses such as BlackEnergy and will avoid disruptive activities or services.
ALL-IN-ONE protects ICS ENDPOINTS' as a whole, servers,
communication networks through which data and instructions pass, data itself, terminals and
individual components.
2. ZERO TRUST ARCHITERTURE
The ZERO TRUST ARCHITECTURE of the ALL-IN-ONE system, by partitioning the enterprise network into
sub-systems, namely the enterprise network, control network and industrial network, which are
separated from each other by security devices such as firewalls, ARCHANGEL ONE WAY, reduces the
exposure of industrial infrastructure to threats and prepare systems for enhanced installation
monitoring and incident detection.
Of course, the security of any device, any server, program, data, depends not only on the element of
material protection but also and most importantly on respecting the strict policies governing access
to the installation, its use and behavior in case of a problem.

Figure 4: Zero Trust Architecture & Micro segmentation of ALL-IN-ONE protect DATA: They are in
a DMZ (Demilitarized Zone)
But, thanks to the ZERO TRUST architecture and the elements that made it up,
including the ARCHANGEL ONEWAY, or SP-One, there will be no more:
- Disruption in the services or operation of the ICS for example, due to blockage, delay in the flow
of information, destruction or malicious encryption
- Unauthorized modifications to the system or its deactivation due to unfriendly penetrations or
instructions that are illegal and harmful and which are of a nature such as to cause enormous human,
material or financial damage,