In Industry
To protect the production tool which is controlled by a computer program so that it does not fall victim to a computer attack which would paralyze it for many weeks.


SP-One© is a program and a system that is creating a hermetic secure shelter
around the source code or programs that you are using either in your office, Administration,
at University, in your Cloud, in any mechanic and in SaaS.
SP-One©, thanks to its method, allows you to work with your programs even when such
programs are hosted in a hermetic shelter.
And, one of the most important benefits of SP-One© is that even if you are victim of a
ransomware and during and after such attack , THERE WILL BE NO DISCONTINUITY in your work,
your production, and your services:
1. The hospitals will continue to care,
2. The Industry will continue to produce,
3. The University will continue to work,
4. The Public Services will not stop.
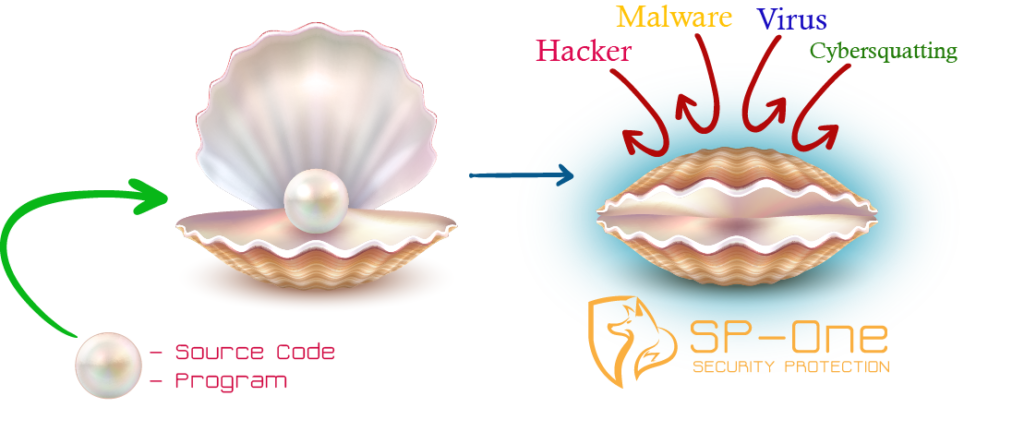
The best way to explain how SP-One© works is to compare it to the shell of an
oyster in which the program that needs to be protected is the oyster: The protected element
is enclosed in its shell which protects it from malicious penetration.
SP-One© allows the protected program to function normally just as if it were not protected.
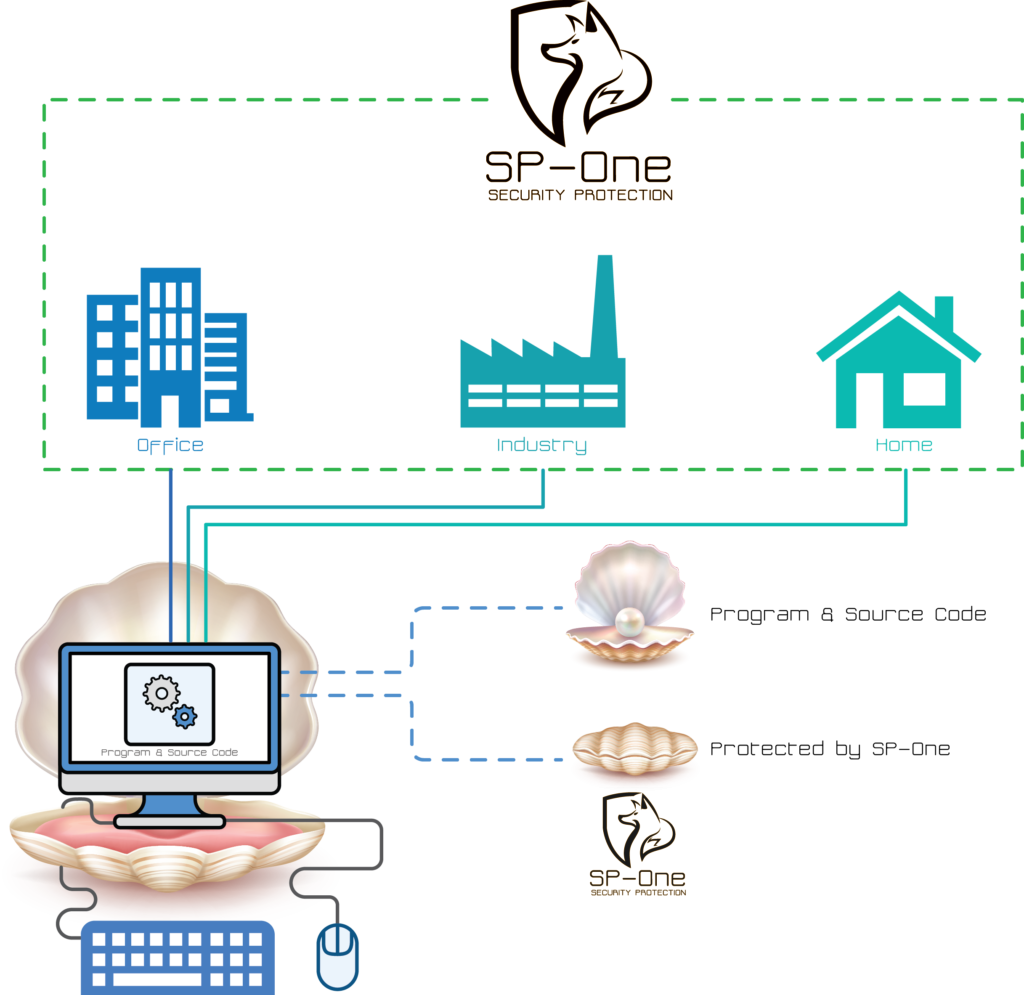
SP-One© is a program that can be downloaded and that will protect programs,
folders, codes that you will want to see protected from any type of attack or theft.
Its use is very simple since you just have to indicate what must be protected and the
SP-One© folder selector will do the rest. A tutorial obviously accompanies the program.
SP-One© is a totally secure program that has no back door and, like all PT SYDECO
products, does not involve any third party.
To protect the production tool which is controlled by a computer program so that it does not fall victim to a computer attack which would paralyze it for many weeks.
To avoid interruption in care, to save lives
To protect software that is among the most coveted prey of hackers.
To avoid interuption in services, To help people who need such services
To protect IoT, Smart home against any attempt of taking control of it, and to protect the home work against any attempt of misusing or steeling it.

.png)