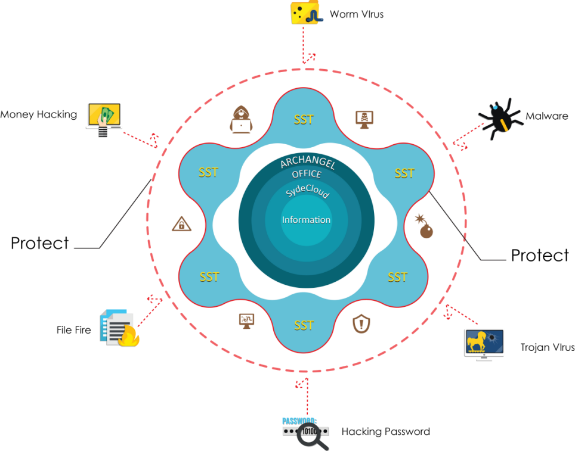
WHY ARCHANGEL?
Because the Outside world is full of danger


ARCHANGEL©2.0 Next Generation Firewall is:
ARCHANGEL2.0© NGFW uses more advanced technology than traditional firewalls, making it better at identifying and blocking advanced threats. It can also inspect and block traffic based on specific applications, even if they use non-standard ports. This makes it more effective at preventing attacks that other firewalls might miss.

The benefit of having a firewall, and particularly a next-generation firewall like ARCHANGEL2.0© NGFW, is that it helps protect your computer or network from threats that can cause damage, such as stealing your personal information, installing malware, or disrupting your system. This protection can help prevent financial losses, data breaches, and other negative consequences.
A next-generation firewall like ARCHANGEL2.0© NGFW is intended for anyone who wants to protect their computer or network from advanced threats. This can include individuals, small businesses, and larger organizations. Anyone who uses the internet should consider using a firewall to protect themselves and their data.
The fundamental principles on which our defence system is based are ZERO TRUST and
MICRO-SEGMENTATION, as well as the rule that nothing can enter the private network
without system authorisation.
6. Advanced malware detection: In the system of ARCHANGEL, we do not need to analyze the types of intrusion because the system blocks everything that is suspicious coming from the outside world and anything that is suspicious that could be coming from a device in the private network.
As we could already point it out, we don’t trust the users so all users are suspicious and all the traffic going inside or outside the network is analyzed by the system.
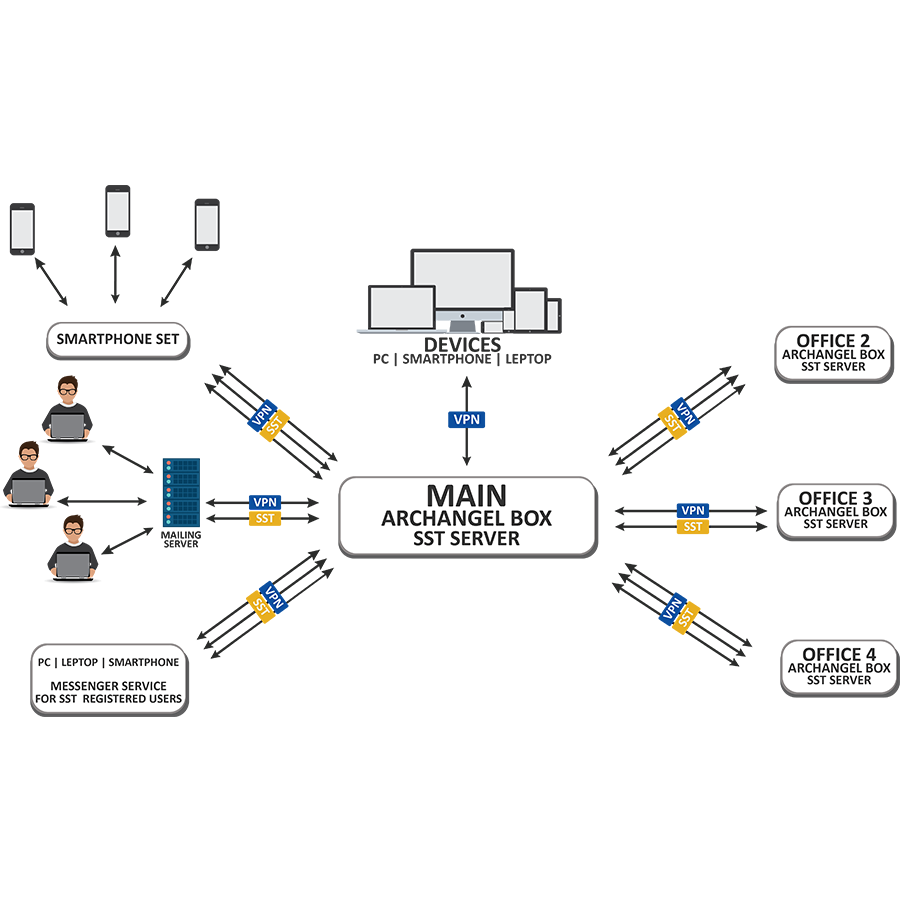
All devices in the private network are connected by VPN tunnels to the VPN server located in ARCHANGEL. To reach the VPN server, data must pass through one of the firewalls and be examined by an intelligent agent before reaching another device inside or outside the network.
In addition to ARCHANGEL© Firewall of Next Generation, ARCHANGEL Integrate Protection System 2.0 includes SydeCloud©.
SydeCloud© is the Online File sharing and backup system of PT SYDECO.
SydeCloud© server is protected by ARCHANGEL Firewall and SST, the system of encryption of PT SYDECO that is no using any key.
Thanks to SydeCloud, work can be remotely. You can access your data where you are and give access to who you want. A space of 2GB is allocated to each user. There is no third party that intervenes. All your data are secure and stay in your office or in the company. Also, there is no charge when using SydeCloud©.
I – TO PROTECT THE INFORMATION SYSTEM:
By creating a private network, Archangel© protects the device from cyber-attacks and prevents lateral spread of virus contamination. Artificial Intelligence embedded in the system gives Archangel the ability to make decisions.
• EACH SECONDARY ARCHANGEL BOX IS GIVING
THE SAME PROTECTION AS THE MAIN SERVER
• ARCHANGEL PROTECTS THE DEVICES AND CREATES VPN.
II – TO PROTECT THE INDUSTRIAL NETWORK:
The fundamental rule to be observed in interconnections between different networks is PARTITIONING, regardless of the type of network to which the industrial network must be interconnected. The best way to partition a network is to protect it with a FIREWALL, but not with just any firewall. This firewall must in fact be able to withstand increasingly sophisticated attacks, even those carried out from a quantum computer, and must be able to protect the data collected by the installation if it has this effect, and above all it must be unidirectional when it comes to protecting an installation of class 1 or 2.
This partitioning must be unidirectional in the case of an installation of class 1 from the industrial system to any other network, including another industrial network of the same company or institution, whether of lower class or of the same class.
CLASS 1: Companies which consist of only one department with a single programmable installation or which have several departments with such installations which are interconnected and for which this installation or these installations constitute(s) the main activity.
This partitioning must also be unidirectional in the case of an installation of class 2 from the industrial system to a public network or to another industrial network of class 3.
CLASS 2: Companies which comprise more than one department and whose connected and/or programmable installations are not interconnected with each other but for which such facilities constitute the principal activity.
The system developed by PT SYDECO, ARCHANGEL OW©, meets all these requirements in that it allows the unidirectional and is completely impermeable to the attacks led even by a quantum computer because its protection and that which it provides are not based on theory of numbers.
ARCHANGEL is part of the
ALL-IN-ONE IT
Security Solution from PT SYDECO which is a
ZERO TRUST ARCHITECTURE
designed to prevent cyber-attacks such as Ransomware or data breaches. The ICS
endpoints of the SCADA (Supervisory Control And Data Acquisition) or DCS (Distributed Control
System) can be protected by the ALL-IN-ONE system developed by PT SYDECO, which will avoid
interrupting activities or services for several days.

PT SYDECO INDONESIA
.png)