POST QUANTUM SECURITY OF DATA
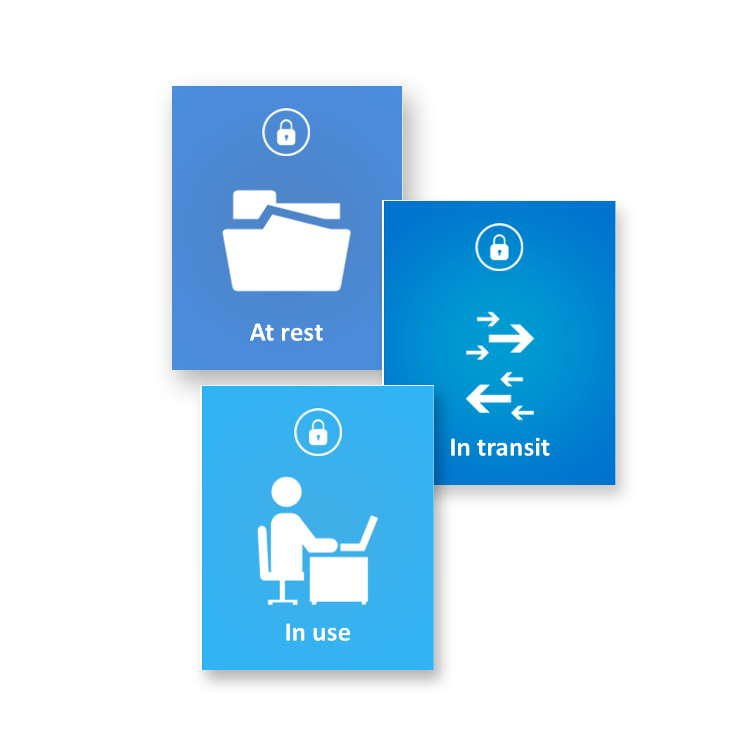
DATA AT REST
Because the SST© Post Quantum Encryption Method uses no keys and does not
rely on
mathematical operations or number factoring, a quantum computer cannot break the protection
it offers to
data.
The SST post-quantum encryption method applied to protect your data and
keeps it safe in
a quantum world.
The SST post-quantum encryption method is a QUANTUM SAFE CRYPTOGRAPHY.
DATA IN MOTION
The VPN that ARCHANGEL creates is a QUANTUM-SAFE
VPN,
because its technology is not based on cryptographic protocols that can be hacked. Indeed
ARCHANGEL’s VPN
does not use any key either symmetric or asymmetric but the
SST
technology that is not based on any mathematical operation.
Data are therefore fully protected even when they are in motion









.png)